Bridging the gap Combining Cloud and On-Premise Security with C4SAM...
Read MoreA quick 5 step guide for everyone who is not familiar with the NIST Framework.
What is the NIST Cyber Security Framework (CSF)?
The NIST CSF is a set of guidelines, to help organisations construct and/ or ameliorate their “cyber hygiene”. The Framework gives a set of standards and recommendations that help organisations to identify, prevent, recover, and respond to cyberattacks.
Here is a quick start-up guide to get started with the NIST CSF from today!
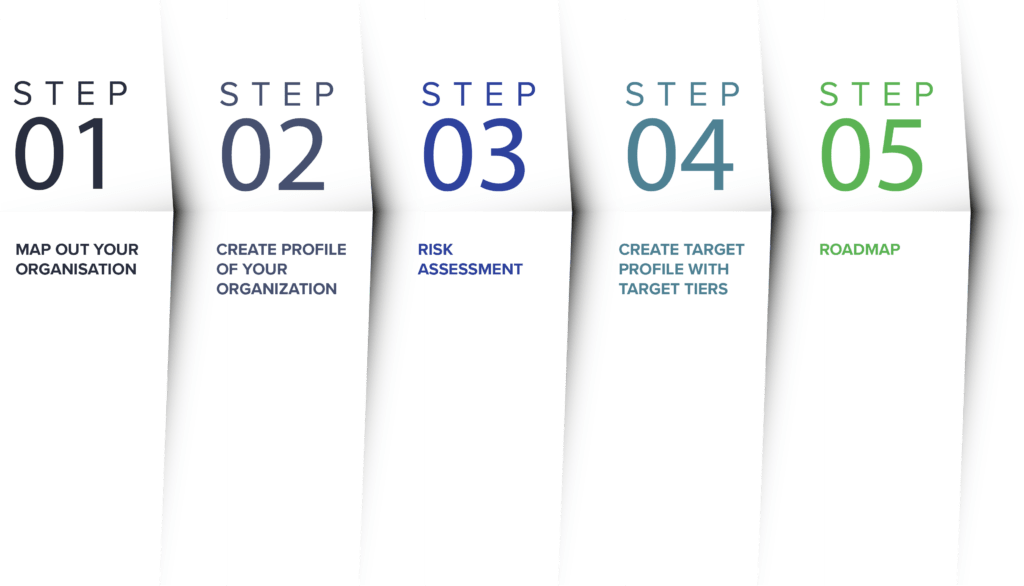
Step 1 - Map Out your organisation
First of all, when planning to implement the NIST framework in your organisation, it is important to understand your organisation, not just internally but also externally. Who are your suppliers and who are your customers? What is your organisation hierarchy? All of these are important when implementing any Cybersecurity framework. The main idea is you are now starting to implement the NIST framework, but where? Identify all of these areas and this will be important later on in securing systems. It’s important that everyone knows their role to play and are aware of who to go to when there is an issue.
Maybe a specific area has sensitive data, it will be important to protect the data’s confidentiality, and this should be prioritised over the accessibility or the integrity of that data. Understanding the goals and drivers are key to start implementing the NIST framework.
Step 2 - Create a profile of your organization
What is your current organisation profile?
This is where you start to really dig into your organisation’s security, this is not defined by NIST so this is an internal document (can be in any form). This document is not about risks or what you should be doing, but what you are doing today. It’s important to understand what you are doing to start finding improvements in your organisation.
Step 3 - Risk assessment
Here you want to think about what risks are associated with what part of the business, is it the whole business or is it a certain part of it. These risks will change with regulations and as cybersecurity evolves. What are the threats? What are the vulnerabilities.? What would happen if ….? Will it be a loss of data, loss of services, what would go wrong? Make sure this information is recorded.
Then we look at the likelihood of the threats and if it would happen, how bad would it be? Is it going to be a quick 2-click fix or is it going to take multiple people a whole day to fix? Also, what are the impacts on the organisation, customers, etc.
Step 4 - Create target profile with target tiers
What is your target profile?
This is where you want to be writing down your priorities. Starting with high-risk and high-likeliness of occurring, and then finishing with low-risk, and low chance of occurring. If the previous steps were done well this should be straightforward. There are no requirements for how detailed it is but it should be detailed enough to understand where you want to be ideally.
Finding out what Tier you are in here see here:
Cybersecurity Framework Tiers
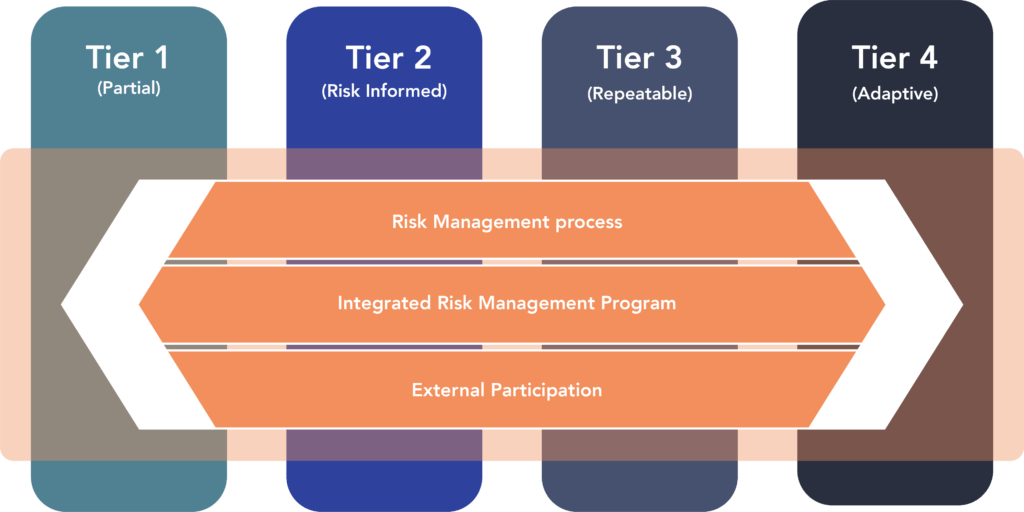
For organizations that are new to cybersecurity and think that they aren’t doing anything in their organization, this is not true, every organization has computer passwords, an antivirus, and don’t use their next-door coffee shop’s WIFI as internet access right?
Step 5 - Roadmap
This is where “the rubber meets the road;” we take the gaps prioritised in the previous step and a roadmap is made. Write down who will implement what goal and a “Who, What, When, Where and Why” approach can be a good way to start if you are new to CS. The roadmap should be visible and it should available for the relevant departments.
This is a great way to start your journey in integrating good cybersecurity standards in your organisation, to get a good list of subcategories and documents straight from NIST themselves checkout this link:
https://www.nist.gov/cyberframework/online-learning/components-framework
Here you can find more details on the “cores” to help you with your risk assessment! Good luck!
Other blog posts
Critical Boot Loader Vulnerability in Shim
Critical vulnerability in the Shim boot loader What to do?...
Read MoreCybersecurity Trends 2024
Cybersecurity trends 2024 Intelligent & Resilient – Security through Automation...
Read MoreCybersecurity Kill Chain
What is a Cybersecurity Kill Chain? understanding, detecting, and preventing...
Read MoreWhy should SMEs be interested in cybersecurity awareness
Why should anyone target us? Why should SMEs be interested...
Read MoreTop 8 Prediction for Cybersecurity within the next 2 years
Top 8 Prediction for Cybersecurity within the next 2 years...
Read More