Bridging the gap Combining Cloud and On-Premise Security with C4SAM...
Read MoreZeroday vulnerabiltity in openssl - What to do?
As you may all have heard, OpenSSL released security recommendations to address two new vulnerabilities, CVE-2022-3602 and CVE-2022-3786, affecting OpenSSL versions from 3.0.0 to 3.0.6.
Both vulnerabilities might cause a denial of service. According to them, a cyber threat actor leveraging CVE-2022-3786, might craft a malicious email address to overflow four attacker-controlled bytes on the stack. This buffer overflow could result in a crash, which causes a denial of service (DDOS) or potentially remote code execution (RCE), allowing them to take control of a system, that is affected.
What is DDOS?
DDoS (Distributed Denial of Service) are malicious cyber-attacks that cybercriminals employ in order to make an online service, network resource or host machine unavailable. These incidents are closely associated with botnets, where hackers take over command and control of thousands of Internet-connected devices, and then in coordinated attacks, direct all those devices to simultaneously send requests to the target.
What is RCE?
Remote code execution (RCE) attacks allow an attacker to remotely execute malicious code. The impact of such a vulnerability can range from malware execution to an attacker gaining full control over a compromised machine.
Therefore, CISA encouraged users to review the OpenSSL advisory, blog, OpenSSL 3.0.7 announcement, and upgrade to OpenSSL 3.0.7. For additional information on affected products, see the 2022 OpenSSL vulnerability – CVE-2022-3602 GitHub repository, jointly maintained by the Netherland’s National Cyber Security Centrum (NCSC-NL) and CISA.
While the community was afraid that this might be comparable to the Heartbleed vulnerability in 2014, OpenSSL has now downgraded the severity of the current vulnerabilities from ‘critical’ to ‘high’.
Since there is no patch or workaround, according to GDPR, companies` CIOs or CSOs must immediately take all systems that are affected by this vulnerability offline.
But how do you know which systems are affected?
Ask c4sam 42
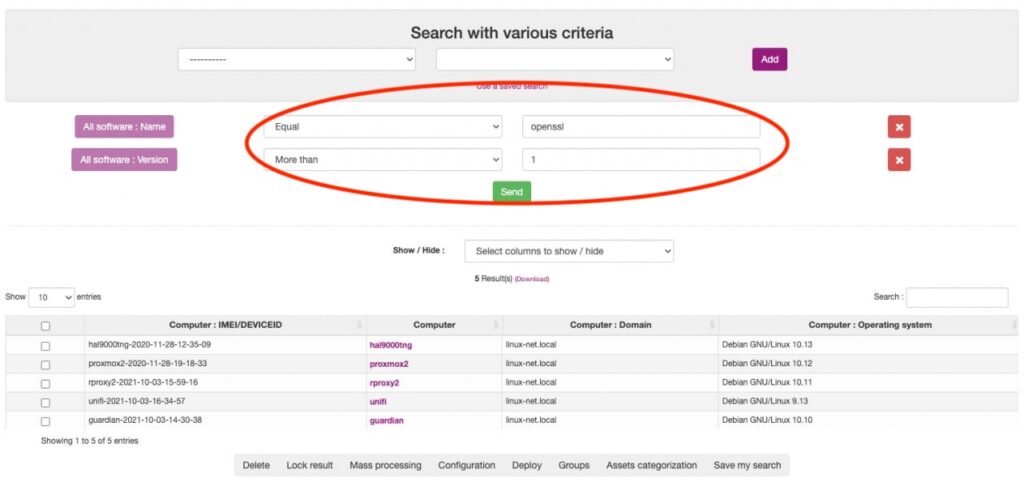
Through an automated inventory identification, which can easily be conducted with our solution.
Smart filter – installed versions < 3.xxx are not affected.
Other blog posts
Critical Boot Loader Vulnerability in Shim
Critical vulnerability in the Shim boot loader What to do?...
Read MoreCybersecurity Trends 2024
Cybersecurity trends 2024 Intelligent & Resilient – Security through Automation...
Read MoreCybersecurity Kill Chain
What is a Cybersecurity Kill Chain? understanding, detecting, and preventing...
Read MoreWhy should SMEs be interested in cybersecurity awareness
Why should anyone target us? Why should SMEs be interested...
Read MoreTop 8 Prediction for Cybersecurity within the next 2 years
Top 8 Prediction for Cybersecurity within the next 2 years...
Read More