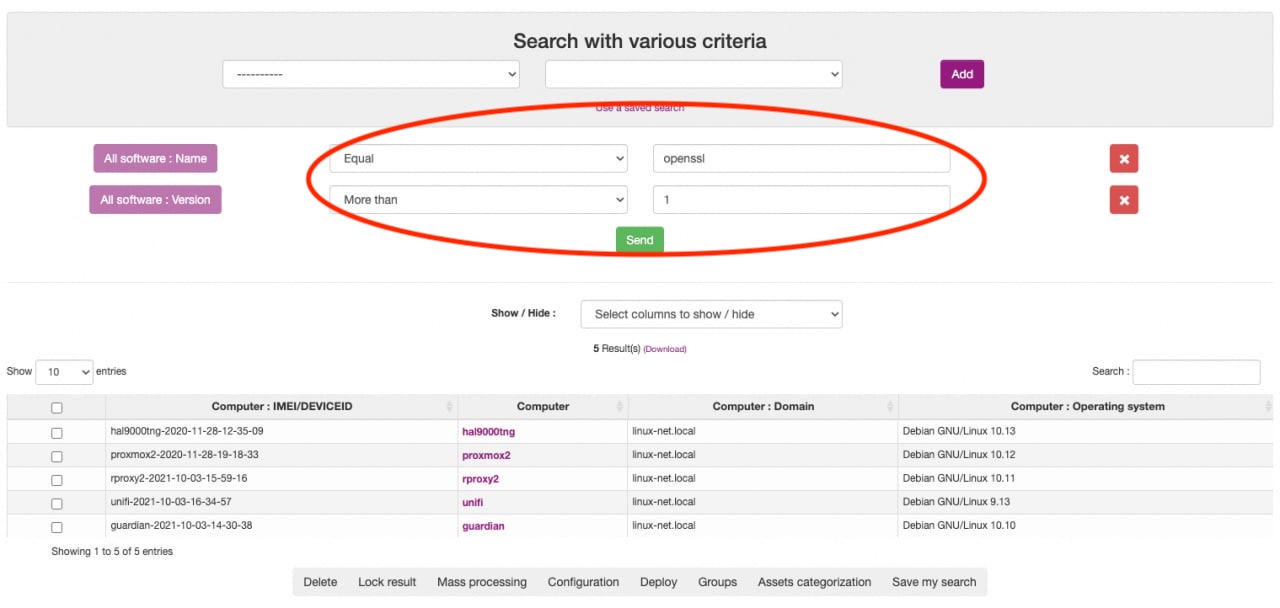
SMBs are much more likely to be attacked
SMBs are much more likely to be attacked by cybercriminals than large companies While cyber-attacks on large companies are in the news, attacks on SMBs are rarely heard of. And that even though SMEs in particular are a popular target for cybercriminals. It is high time for small and medium-sized companies to protect their IT…
read more